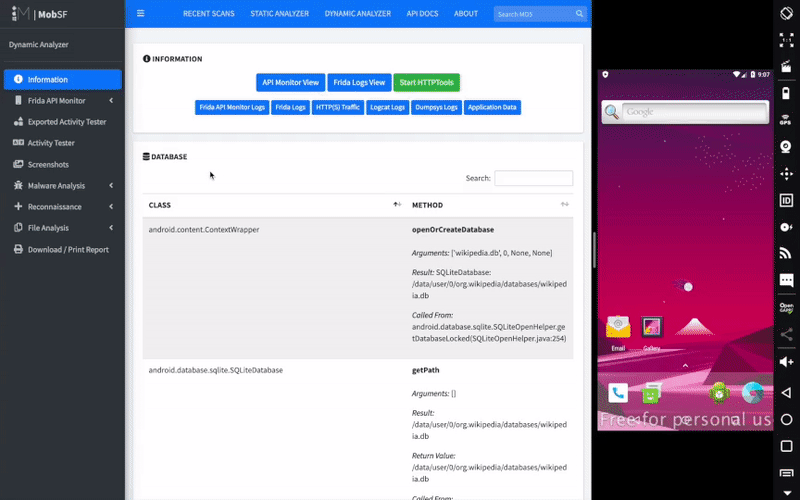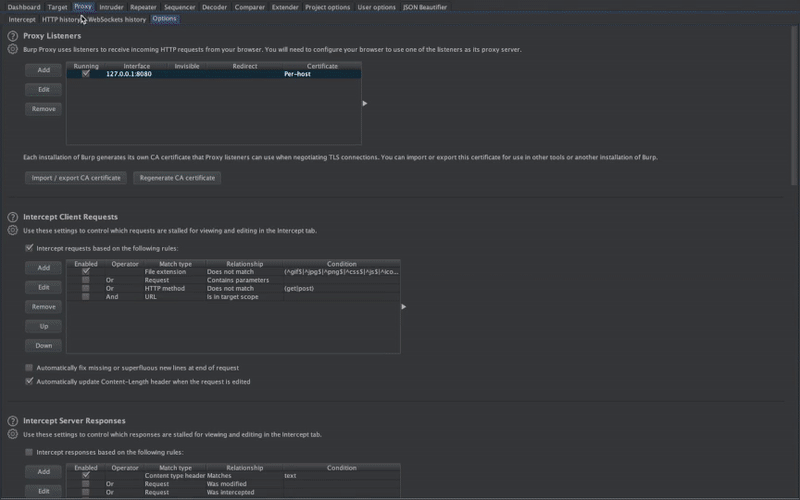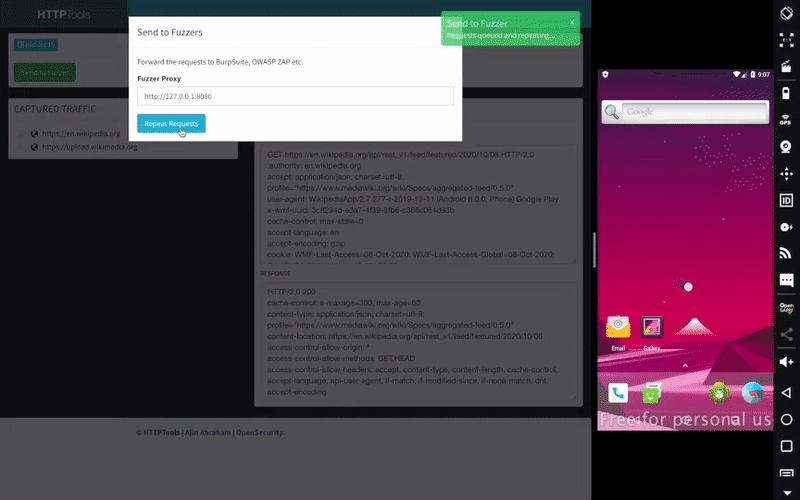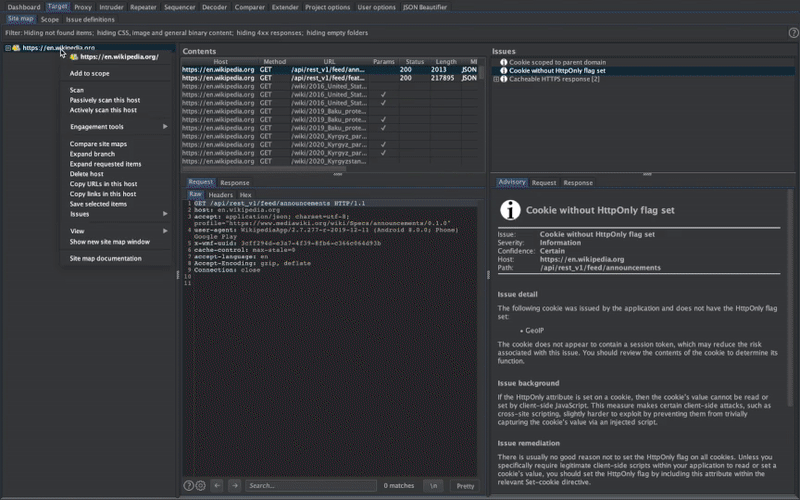
Mobile Security Framework (MobSF) is a security research platform for mobile applications in Android, iOS and Windows Mobile. MobSF can be used for a variety of use cases such as mobile application security, penetration testing, malware analysis, and privacy analysis. The Static Analyzer supports popular mobile app binaries like APK, IPA, APPX and source code. Meanwhile, the Dynamic Analyzer supports both Android and iOS applications and offers a platform for interactive instrumented testing, runtime data and network traffic analysis. MobSF seamlessly integrates with your DevSecOps or CI/CD pipeline, facilitated by REST APIs and CLI tools, enhancing your security workflow with ease.
MobSF is also bundled with Android Tamer, BlackArch and Pentoo.
Has MobSF made a difference for you? Show your support and help us innovate with a donation. It's easy to build open source, maintaining one is a different story.
Long live open source!
Quick setup with docker
docker pull opensecurity/mobile-security-framework-mobsf:latest
docker run -it --rm -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
- Try MobSF Static Analyzer Online: mobsf.live
- MobSF in CI/CD: mobsfscan
- Conference Presentations: Slides & Videos
- MobSF Online Course: OpSecX MAS
- What's New: See Changelog
Ajin Abraham  | Magaofei
| Magaofei  | Matan Dobrushin
| Matan Dobrushin  | Vincent Nadal
| Vincent Nadal 
 Automated Mobile Application Security Assessment with MobSF -MAS
Automated Mobile Application Security Assessment with MobSF -MAS
 Android Security Tools Expert -ATX
Android Security Tools Expert -ATX
- Free Support: Free limited support, questions, help and discussions, join our Slack channel
- Enterprise Support: Priority feature requests, live support & onsite training, see
- Read CONTRIBUTING.md before opening bugs, feature requests and pull request.
- For Project updates and announcements, follow @ajinabraham or @OpenSecurity_IN.
- Github Issues are only for tracking bugs and feature requests. Do not post support or help queries there. We have a slack channel for that.
- Amrutha VC - For the new MobSF logo
- Dominik Schlecht - For the awesome work on adding Windows Phone App Static Analysis to MobSF
- Esteban - Better Android Manifest Analysis and Static Analysis Improvement.
- Matan Dobrushin - For adding Android ARM Emulator support to MobSF - Special thanks goes for cuckoo-droid
- Shuxin - Android Binary Analysis
- Abhinav Saxena - (@xandfury) - For Travis CI and Logging integration
 Netguru (@karolpiateknet, @mtbrzeski) - For iOS Swift support, Rule contributions and SAST refactoring.
Netguru (@karolpiateknet, @mtbrzeski) - For iOS Swift support, Rule contributions and SAST refactoring.- Maxime Fawe - (@Arenash13) - For Matching Strategy implementation of SAST pattern matching algorithms.
- Abhinav Sejpal (@Abhinav_Sejpal) - For poking me with bugs, feature requests, and UI & UX suggestions
- Anant Srivastava (@anantshri) - For Activity Tester Idea
- Anto Joseph (@antojoseph) - For the help with SuperSU
- Bharadwaj Machiraju (@tunnelshade) - For writing pyWebProxy from scratch
- Rahul (@c0dist) - Kali Support
- MindMac - For writing Android Blue Pill
- Oscar Alfonso Diaz - (@OscarAkaElvis) - For Dockerfile contributions
- Thomas Abraham - For JS Hacks on UI
- Tim Brown (@timb_machine) - For the iOS Binary Analysis Ruleset
- Shanil Prasad (@Rajuraju14) - For improving iOS ATS Analysis
- Jovan Petrovic (@JovanPetrovic) - For sponsoring a server to host mobsf.live