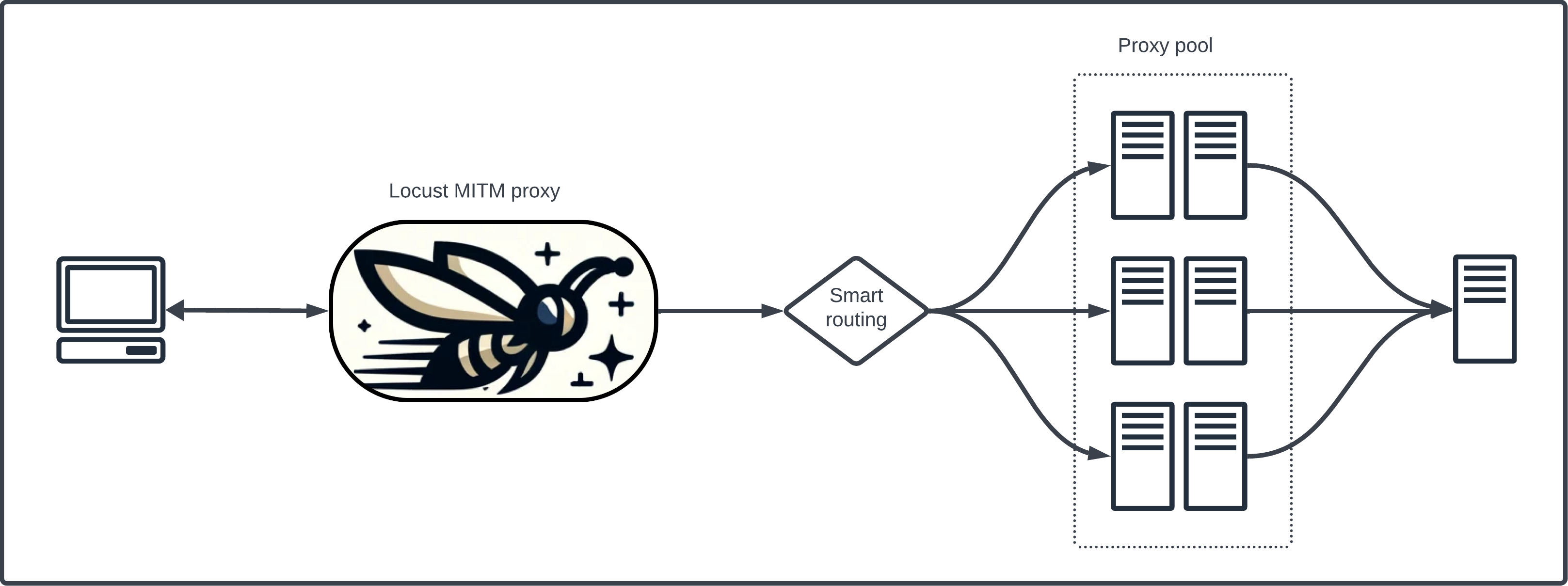
Locust is a MITM proxy that routes traffic to various upstream proxies. Locust comes with a CLI that facilitates proxy configuration, importing, querying, and creating custom Squid proxies that are automatically used by the proxy server.
See releases for binaries and installation instructions.
- Proxy server that smartly routes traffic to an appropriate upstream proxy.
- Easily configurable via a tagging system.
- CLI that makes managing proxies easy.
- File importing that works out of the box with known proxy providers.
- Squid proxy farm commands that allow for the creation, deletion, and cycling of squid VMs that are automatically picked up and used by the server (currently only works with GCP).
- Configuration commands that make sure your proxies work out of the box.
- Querying via tags that gives visibility into proxies without having to execute SQL.
Locust is a super proxy that maintains a pool of upstream proxies that it uses to route traffic to the requested web resources. As a user, you use it like any other proxy. When Locust receives a web request it analyzes the target URL and determines which proxy is best for the given request.
Locust keeps track of metadata and metrics about every web request it completes in order to continually fine tune which proxies to use and remove bad ones. You can also tag web domains in order to instruct Locust to limit the pool of proxies it will choose from for requests to these domains.
Via the CLI, you can also create and cycle Squid proxies in your GCP account which Locust will automatically start using as they are created.
gloudCLI installed and authenticated.- using the
farmcommand will require sufficient GCP privileges for VM creation and destruction. - ENV vars set with the proper PostgreSQL connection parameters. See
.envfile for default settings.
The proxy server currently runs as a dockerfile. A compose file is provided as well for easy spinup. Without the compose you will need ENV vars set with the proper PostgreSQL connection parameters. See .env file for the default settings.
locust-cli -h
Docker compose:
docker-compose up --build
Docker image can be ran without compose, but you must ensure that it is provided with ENV vars for PSQL connection parameters.
Locust uses its own self-signed certs for HTTPS requests. In order to use Locust as a trusted CA, you must add its cert as a trusted source in your OS keychain.
- Open
locust/src/ca/locust.cerwith Keychain Access app. - Double-click the Locust cert.
- Set the Trust option to
Always Trust.